Beginners IT-Security Guide
March 16, 2012 29 Comments
![]() In 21st Century we need not ONLY talking about Internet-Safety, Online-Safety and IT-Security, but we need to secure our computers and ANY other related device connecting to Internet, such as also our smartphones! I will present you now a tutorial on How-To create best protection (as on March 2012) for your computer and this with mostly FREE tools and FREE Online Services… Also will I provide you a worksheet which helps you planning your weekly tasks!
In 21st Century we need not ONLY talking about Internet-Safety, Online-Safety and IT-Security, but we need to secure our computers and ANY other related device connecting to Internet, such as also our smartphones! I will present you now a tutorial on How-To create best protection (as on March 2012) for your computer and this with mostly FREE tools and FREE Online Services… Also will I provide you a worksheet which helps you planning your weekly tasks!
.
Weekly Tasks? YES, you need to work a bit, but don’t worry, most tasks are automated and don’t need a lot of intervention! But they are necessary! It’s ONLY the first time when you have to install some programs and to read this tutorial that you will need to invest time!
===> But investing once time for saving time later and avoiding trouble is definitely worth to do 😉 <===
.
What you should know: Computer Viruses and Threats
.
Check the video for better understanding, click image… This video explains the how computer viruses, worms and trojans work and what you can do to protect yourself.
.
Click image above to access video
.
===> For readers who don’t want to read (trusting me and only want to install the programs which they didn’t know yet…), but ONLY want to install the proposed programs: go to the bottom of this tutorial and follow the download links! <===
So here we go…
First a reminder and the most important to know to have best protection on your computer:
|
So, after knowing now what’s most important for protecting your computer and helping also your Government for a better National Cyber-Security we will start with our workshop on How-To protect our computer at its best (for private users…)…
Related links:
First of all, I suggest to you to check online your computer’s security to get convinced yourselves about the need to secure your computer, here we go…
Most of this advice is for Windows PC’s, but some are also necessary for Mac and Linux computers!
1. Is your Browser up-to-date?
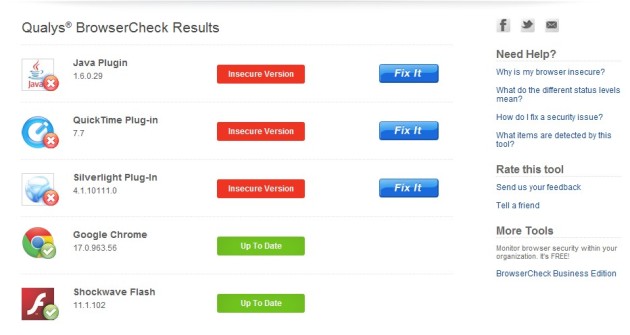
This is very easy to check online, without installation of any program! Use Qualys BrowserCheck who will perform a security analysis of your browser and its plugins to identify any security issues.
.
===> Here is the link: Qualys Browser Check <===
`
2. Is your Operating System switched to automatic updates?
This is the most important for any OS (Operating system), the updates!!! They MUST get installed!!!
===> Visually: it’s like of the manufacturer of a car has detected technical problems who are necessary to get fixed for your security! The car will then go the the garage and problems will get fixed for FREE! <===
Read instructions on How-To:
3. Is your antivirus program up-to-date?
Surprised? I am convinced that most of you are wondering and surprise about the results! So now you know that it is about time to get better protected, follow these steps now please:
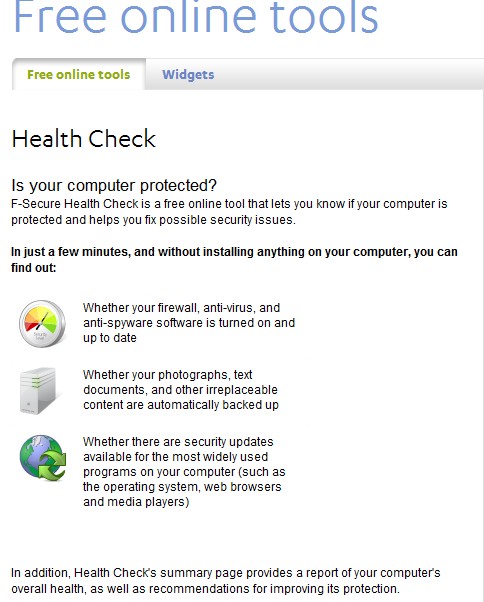
Run F-Secure HealthCheck http://www.f-secure.com/en/web/home_global/protection/free-online-tools/free-online-tools
.
4. Install an “Internet Security Suite”!
Instead of working with a FREE antivirus, use a “Internet Security Suite“! Why?

.
Links to learn more:
- https://gustmeesen.wordpress.com/2012/01/05/pc-security-howto-secure-my-pc/
- Why ICT Security? Why the need to secure a computer?
- AV-Comparatives.org
- On this site you will find independent comparatives of antivirus software. All products listed in our comparatives are already a selection of some very good anti-virus products. In order to get included in our main tests, vendors must fulfill various conditions and minimum requirements.
5. Update your Third Party Applications!
Third Party Programs are responsible for 78% of vulnerabilities!!! What are Third Party Applications (Programs)? Knowing that third party programs are vulnerable also, we must update them also! Use SECUNIA PSI to update automatically third party programs, install it ===> https://secunia.com/ <===
.
.
6. Organize a Family Weekly-Security-Day
My suggestion: to make sure that anybody’s computer is secure at home I suggest that you introduce a “Family Weekly-Security-Day“, where any week one member of your family will get chosen as the “responsible” for the week and that “responsible” will remind you to respect the weekly task and controls also that the task was achieved! I will provide you with a sheet from Google Docs which you can use for it…
===> Play as a team in the family to make sure that everybody respects the weekly Security-Day! Any week someone else is responsible to remember the whole team (family) for the Weekly-Security-Day-Task! <===
Worksheets on Google Docs:
- Weekly Family-Security Day (Google Docs Spread Sheet)
- Week Responsible Planner (Google Docs Spread Sheet)
You can even imagine some penalties such as e.g. making the dish-wash for 2 days, or similar, LOL 😉
.
===> Motivation: don’t let us forget the positive side and motivate members of family to do that unusual task by giving them some special bonus points when well done that task! Those bonus points could result in: <===
.
- Penalties could get reset for a certain time (up to you to make the rules…)
- Bonus points will get collected and by reaching a certain score will result by paying out some money (up to you to say how much…)
- Your own ideas for motivating the team to do the tasks…
7. Secure Surfing Behavior
McAfee SiteAdvisor™ software
McAfee SiteAdvisor™, software is an award-winning, free browser plug-in that gives safety advice about Websites before you click on a risky site. These site ratings are based on tests conducted by McAfee using an army of computers that look for all kinds of threats (detailed below). The result is a guide to Web safety. The SiteAdvisor software is free, easy to install and even easier to use. And it doesn’t collect any personally identifiable information.
Other similar products:
8. Forewarned is Forearmed
In a world where ICT is getting more and more important it is very important to follow the Information (“I” in ICT) and also to share this Information over the Social Medias (“C” in ICT), communicating with your friends in real life and in virtual life (Internet)!
Recommended programs:
- FeedBurner (Google)
- NewZie
9. Change your Router’s Pass Word!
Cybercriminals may also use your Router (without that you know it…) when you haven’t changed the original settings! Text from Internet / Network Security:
.
===> The first step in securing your wireless network is the same as the first step for just about everything else in computers and computer networking — always change the defaults. Any attacker can find out what the default username and password is for a given program or device in just a few minutes. <===
10. Chose strong PassWords
11. Be Aware of Public Wi-Fi!!!
Get behind the SHIELD! 100% FREE!
- Secure your web session, data, online shopping, and personal information online with HTTPS encryption.
- Protect yourself from identity theft online.
- Hide your IP address for your privacy online.
- Access all content privately without censorship; bypass firewalls.
- Protect yourself from snoopers at Wi-Fi hotspots, hotels, airports, corporate offices.
Works on wireless and wired connections alike. Provides Unlimited Bandwidth.
Works on the PC and the Mac, including new operating systems (Windows 7 and Snow Leopard)
Hotspot Shield protects your entire web surfing session; securing your connection at both your home Internet network & Public Internet networks (both wired and wireless). Hotspot Shield protects your identity by ensuring that all web transactions (shopping, filling out forms, downloads) are secured through HTTPS. Hotspot Shield also makes you private online making your identity invisible to third party websites and ISP’s. Unless you choose to sign into a certain site, you will be anonymous for your entire web session with Hotspot Shield. We love the web because of the freedom that it creates to explore, organize, and communicate. Hotspot Shield enables access to all information online, providing freedom to access all web content freely and securely. Secure your entire web session and ensure your privacy online; your passwords, credit card numbers, and all of your data is secured with Hotspot Shield. Standard antivirus software protects your computer, but not your web activities.
Here is the address to download it http://hotspotshield.com/.
12. Be aware of what YOU publish online
.
This video reveals the magic behind the magic, making people aware of the fact that their entire life can be found online.
.
.
Don’t want to read all the above text and start the practice?
.
|
..
This below is the situation actually, now you know where it is necessary to apply above mentioned advice
.
Click image to access IKARUS Security Software
.
.
|
.
. as on Friday May 18, 2012: SaferOnlineTeam@MS
.
Follow Friday – Follow
. PS: SaferOnlineTeam@MS Redmond, WA, USA http://www.microsoft.com/security |
.
|
L’auteur Gust MEES est Formateur andragogique / pédagogique TIC, membre du “Comité Conseil” de “Luxembourg Safer Internet” (LuSI), appelé maintenant BEESECURE, partenaire officiel (consultant) du Ministère de l’éducation au Luxembourg du projet ”MySecureIT“, partenaire officiel du Ministère du Commerce au Luxembourg du projet ”CASES” (Cyberworld Awareness and Security Enhancement Structure). The author Gust MEES is ICT Course Instructor, ”Member of the Advisory Board” from “Luxembourg Safer Internet” (LuSI), BEESECURE, Official Partner (Consultant) from the Ministry of Education in Luxembourg, project “MySecureIT“, Official Partner from the Ministry of Commerce in Luxembourg, project “CASES” (Cyberworld Awareness and Security Enhancement Structure). |
.



















Pingback: Malicious Web Apps: How to Spot Them, How to Beat Them | lastsocialmedianews
Pingback: How financial botnets like #Zeus infect computers [video] « Scenario 25 Club
Pingback: Beginners IT-Security Guide | ICT Security-Sécurité PC et Internet | Scoop.it
Pingback: Beginners IT-Security Guide | Free Tutorials in EN, FR, DE | Scoop.it
Pingback: Get smart with 5 minutes tutorials/IT-Security/Part 6: Ideas for a more secure Internet – gustmees
Pingback: Ideas for a more secure Internet-part1/National Security Day as a Family Day – gustmees
Pingback: Visual IT-Security/Learn with videos – gustmees
Pingback: Beginners IT-Security Guide | IT (Systems, Networks, Security) | Scoop.it
Pingback: Beginners IT-Security Guide | 21st Century Learning and Teaching | Scoop.it
Pingback: Beginners IT-Security Guide | TEFL & Educational Technologies | Scoop.it
Pingback: Beginners IT-Security Guide | InfoSec Focus | Scoop.it
Pingback: Beginners IT-Security Guide | Handy Online Tools for Schools | Scoop.it
Pingback: Beginners IT-Security Guide | Love to read, love to learn!
Pingback: Beginners IT-Security Guide | BYOD in Business | Scoop.it
Pingback: Beginners IT-Security Guide | Skolbibliotek | Scoop.it
Pingback: How-To prepare for giving a quality course – gustmees
Pingback: Beginners IT-Security Guide | Vulbus Incognita Geek Zone (GZ) | Scoop.it
Pingback: The Future Internet: Service Web 3.0 « Vicente Montiel Molina
Pingback: Beginners IT-Security Guide | formation 2.0 | Scoop.it
Pingback: Beginners IT-Security Guide « Formation 2.0
Pingback: Beginners IT-Security Guide | Information for sharing | Scoop.it
Pingback: Beginners IT-Security Guide | #ICT news #Cloud #Management #BYOD #BigData #Social Media #Technologies | Scoop.it
Pingback: Beginners IT-Security Guide | Εκπαίδευση και ασφάλεια στο Διαδίκτ&upsi
Pingback: SID2014: Safer Internet Day 2014-Participation – gustmees
Pingback: SID2015: Safer Internet Day 2015-Participation – Education: Digital CitizenShip, CyberSecurity by Gust MEES
Pingback: Naivety in the Digital Age? Social Engineering and OTHER human false beliefs, fails… – Education: Digital CitiZENship, CyberSecurity by Gust MEES
Pingback: SID2016: Safer Internet Day 2016-Participation – Education: Digital CitiZENship, CyberSecurity by Gust MEES
Pingback: SID2017: Safer Internet Day 2017-Participation – EDU: Digital CitiZENship, CyberSecurity, eSkills, Modern EDU by Gust MEES
Pingback: SID2020: Safer Internet Day 2020-Participation – EDU: Digital CitiZENship, CyberSecurity, eSkills, Modern EDU by Gust MEES